修改 Windows 的休眠设定,避免电脑自动休眠
我的电脑在某次更新 Windows 10 之后,原本已设定好不让它自动关机的电脑竟会进入休眠状态! 原因似乎是进入休眠的时间被改动了,而在 Windows 的设定中却不容易找到“休眠”的细部选项!
这 Windows 可真爱找麻烦!
先来看一下 Windows 10 关机选单的 4 个选项做为相关知识:
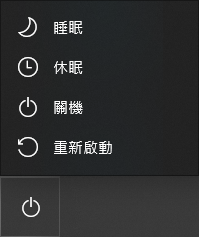
- 睡眠 (Sleep, S3): 会将桌面及应用程式的状态写入至内存,让电脑以极低的耗电方式维持在开机的状态,以便在唤醒电脑时,可以立即回到睡眠前的电脑状态。从 Windows Vista 起,睡眠 (Sleep) 模式已取代了待命 (Standby) 模式。
- 休眠 (Hibernate, S4): 会将桌面及应用程式的状态写入至磁盘再关闭电脑的电源,电脑下次开机会恢复到休眠前的电脑状态。从休眠状态下开机的速度会比睡眠还慢。
- 关机 (Shut down, S5): 关闭所有应用程式并关闭电脑的电源,不会自动储存任何状态。
- 重新开机 (Restart): 关闭所有应用程式并重新启动电脑及作业系统。


近期回响